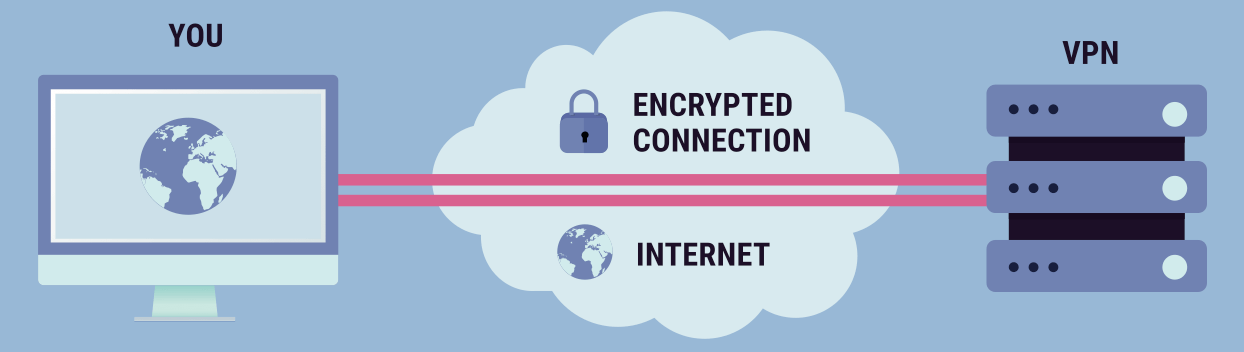
What is a Corporate VPN? To start with a basic, ‘VPN’ stands for Virtual Private Network. It is a network made private in a virtual sense, which uses public telecommunications. In this article we’ll be talking about the public telecommunications device which you are using right now – the Internet!
The purpose of most corporate VPNs is to provide employees who are operating remotely from their office with a secure connection back to the organization’s own network. This is more common than you may think it is. Think of all the police officers, hospital employees and government agencies out there who have information that they would like to keep private.
Why are corporate VPNs set up?
The reason why VPN’s are set up on public telecommunications is due to cost and a need for privacy. Imagine being a mining company with a main office in Vancouver and a branch office at a site in Northern British Columbia. How much would it cost to lay down your own private cable lines, or lease them from a telecommunications company, over all that distance?
A VPN provides a company with a private communication line over a public network. This a much cheaper alternative as all those cable lines are already down, while still getting the amount of privacy desired.
This allows for remote office, and mobile employees to work from anywhere that they can get a connection. For an example that may hit closer to home than a mining company, an employee that is off on a business meeting (like in Arizona, isn’t that where they all happen?) can securely access information on the company server. It is completely impractical to lease a phone line for this short stay, hence why a VPN can be so useful. One with many servers, like the well-reviewed IPVanish VPN, may be a good fit in this example.
How does a corporate VPN keep information private?
A VPN works to keep information private by using security procedures and tunnelling protocols. Three examples of these tunnelling protocols are:
- Point-to-Point Tunneling Protocol – primarily for corporations that want their own network
- Layer Two Forwarding Protocol – Cisco Systems VPN connection for Point-to-Point Protocol traffic
- Layer Two Tunneling Protocol – mainly used when an ISP wants to resell their product
All of these sound technical and intimidating to a newcomer, I’m sure. What you should take away from them is that they open up a ‘tunnel’ through the Internet. The tunnel itself isn’t what is secure, it is the encryption protocol that is passing through the tunnel, and holding your information, that is secure.
What happens when someone wants to steal your information online? If you’re using a VPN and someone were to intercept the information in your session, all they would get from it is a bunch of gibberish. It would be impossible to interpret it as your VPN has the key to translate this encrypted information back into recognizable information.
What is a VPN used for by individuals?
Your information is kept secure during it’s entire trip across the internet, to your company server and back to your remote office and computer. This information can include your:
- Log in and password details
- Banking information
- Secure company documents
- Private photos (of job sites or products in development)
- Private conversations over Skype, Viber, Google Hangouts and any other chat app
- Internet search history, hide your corporate research
VPNs have expanded the privacy of companies dramatically, showing that encryption is not evil or for hackers. No longer will they need to lease lines from the phone company for remote offices, and mobile employees can be completely anonymous and protected no matter where they are.
Take a look at our 10 Best VPN providers and find one that’s the right fit for your corporate needs.
Feature image via MaDedee / Shutterstock